Lost your iPhone or it stopped working? Don’t worry you can still unpair your Apple Watch without a phone. In…
Read More »Technology
Online chat systems have evolved a lot in recent years. We’ve seen the development of platforms like Uhmegle, where people…
Read More »When it comes to purchasing the best gaming mouse, buttons, scroll, and durability are the most important things to focus…
Read More »People are talking about fiber internet and how great it is, but those who haven’t tried it yet might wonder…
Read More »Cloud testing offers a flexible and scalable environment for testing across various devices and browsers. This shift not only accelerates…
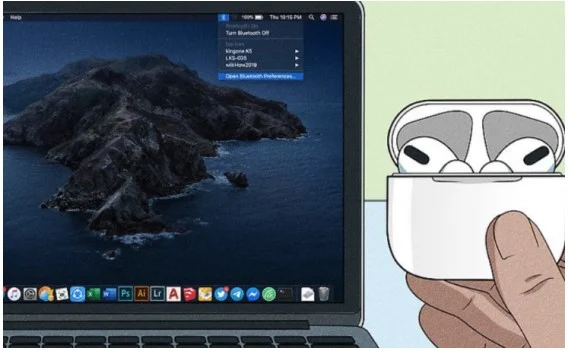
Read More »AirPods have become one of the most widely used wireless audio devices because of the quality and convenience it offers.…
Read More »Software development relies fundamentally on Quality Assurance (QA) to achieve its critical goals. Quality Assurance protects product functionality as well…
Read More »Monday.com is a cloud-based work operating system that facilitates the smooth operation of enterprises. The way individuals run their workplaces…
Read More »Meeting deadlines and producing high-quality applications is a never-ending challenge in the fast-paced world of software development today. Due to…
Read More »Home WiFi services are competing with each other to offer better services to their customers each day. The xFinity Internet…
Read More »